30+ cyber security network diagram
Ad Have a complete network diagram in minutes with Auviks automated network mapping software. Ad Multiple Award Winning Cyber Security Provider in NY and NJ Area.

It Security Certifications Top 30 Certifications In 2019
Ad Are You Concerned with the Risk of a Security Breach in a Changing Landscape of Threats.

. You can edit this template and create your own diagram. Use Createlys easy online diagram editor to edit this diagram collaborate with others and export results to multiple. Ad See why Cybersecurity ROI isnt about cost savings.
Improve your cybersecurity strategy by putting your business first. Access hundreds of templates in Lucidchart and start diagramming in no time. Ad Lucidcharts network diagram software is quick easy to use.
Ad LogRhythm helping you build a high-performance customer-obsessed security organization. Ad Deploy Comprehensive Self-Service Cloud-Based Security to Protect Your Apps. Use PDF export for high.
This basic network security template can help you. - Visualize the components of a basic network. Creately diagrams can be exported and added to Word PPT powerpoint Excel Visio or any other document.
Its about total business impact. Ad Includes Networking Cisco LAN Rack Diagrams. - Understand the flow of information and interactions among network devices.
Supplement an institutions understanding of information flow within and between network segments as well. 112 Current network diagram that. Discovery inventory and documentation that updates in real-time as the network changes.
Import Modify Visio. Reviews speak themselves Thousands of Happy Customers - Contact us Today. Cybersecurity classic by jeremiah Marcoe.
Ad Have a complete network diagram in minutes with Auviks automated network mapping software. An article published on LinkedIn by the National Cyber Security Centre reminded me how I am always amazed that so many o. Discovery inventory and documentation that updates in real-time as the network changes.
A Data Flow Diagram should. Traditional Firewalls Can No Longer Keep Up with Evolving Threats. Lets break DFDs down a little bit.
See How HPE Can Help You Adopt a Zero Trust Framework to Close Gaps and Reduce Complexity.

What Is Network Security Introduction To Network Security Network Security Tutorial Simplilearn Youtube

These Are The 5 Stages Of Growth Hacking Funnel That You Must Pass To Grow Your Business Entrepreneurship Sta Growth Marketing Growth Hacking Growth Medium

Interior Gateway Protocols Cheat Sheet From Cheatography Computer Shortcuts Interior Cisco Networking
What Is Network Topology Types Of Network Topology Bus Ring Star Tree Mesh Simplilearn Youtube

Bar Chart Cyber Security Infographic Template Ppt Keynote Templates
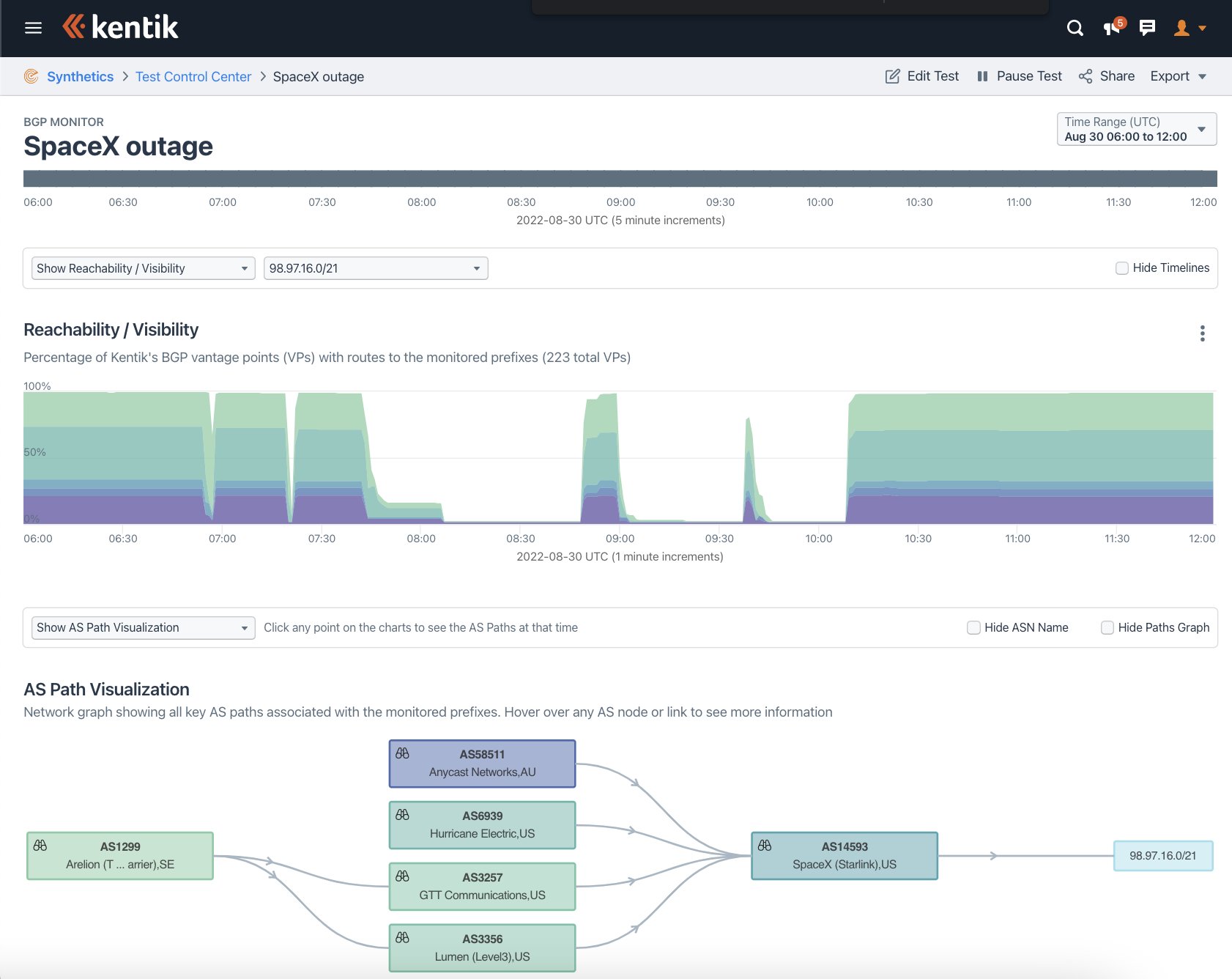
Doug Madory Dougmadory Twitter

Ex 99 2
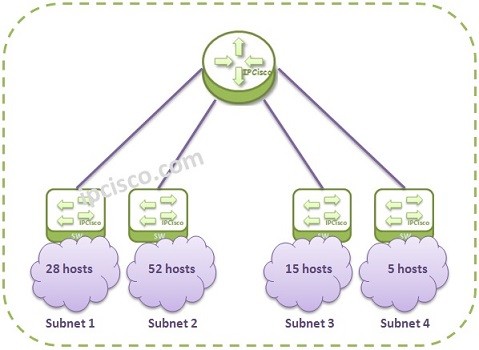
Subnetting Examples 4 Examples Ip Subnetting Overview Ipcisco

Of Cybersecurity Passwords And Staying Safe Online Via Http Wpengine Com Unmasked Football 24 Cyber Security Abc 123

Cyber Security Projects Cyber Security Cyber Networking Basics

Access Programmer Consultants Access Database Relationship Diagram Database Design

Cheat Sheets Packetlife Net Computer Programming Computer Technology Computer Network
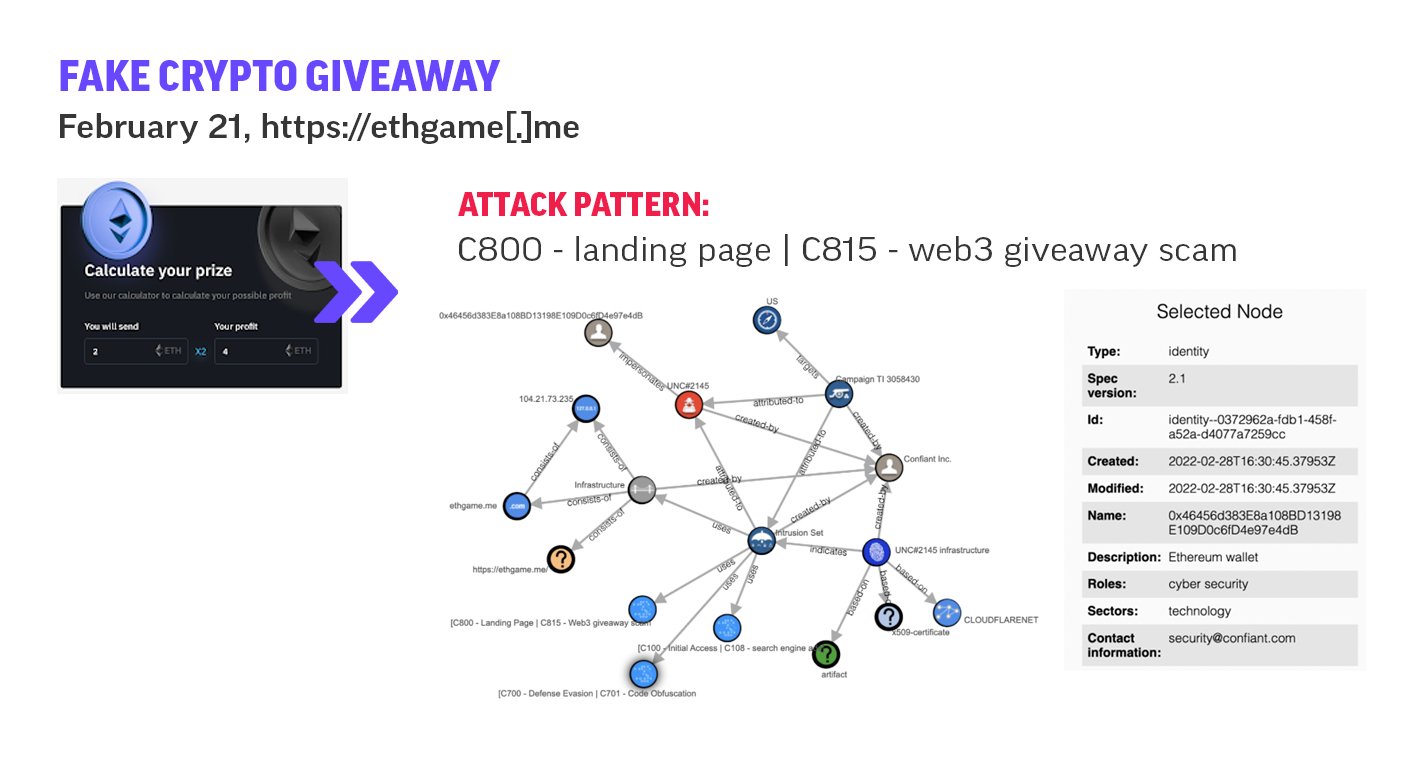
Enterprise Security

Secure And Intelligent Slice Resource Allocation In Vehicles Assisted Cyber Physical Systems Sciencedirect

Access Programmer Consultants Access Database Relationship Diagram Database Design

Cisco Network Diagrams Solution Conceptdraw Com Computer Network Cisco Cisco Networking

4g To 5g Evolution In Depth Security Perspective Youtube